Recently, I successfully obtained the EC-Council CPENT certification. I’d like to introduce this new penetration testing certification, CPENT, which was launched last year. I will also share my thoughts and insights on it. The full article is divided into the following sections:
Introduction to CPENT
CPENT stands for Certified Penetration Testing Professional, clearly indicating that it is a certification for penetration testing. The exam is a hands-on practical test that emphasizes practical skills. It is well-suited for any cybersecurity professionals interested in penetration testing. To obtain the CPENT certification, you need to achieve a score of 70%. Scoring above 90% also grants you the LPT Master certification. This distinction highlights exceptional proficiency in the subject and provides the opportunity to kill two birds with one stone.
According to EC-Council’s previous VAPT roadmap, CPENT is positioned between CEH and LPT, essentially replacing the previous ECSA certification. However, like my previous posts about ECSA, I must reiterate that CEH is not designed specifically for penetration testing. Generally, CEH is not discussed in the context of penetration testing certifications.
Key Focus Areas of CPENT
The detailed course modules for CPENT will be mentioned below. The course and exam topics are all about penetration testing. However, the scope covered by the official announcements is quite broad. On EC-Council’s official website, there is a segment introducing CPENT:

https://www.eccouncil.org/programs/certified-penetration-testing-professional-cpent
In the middle of the webpage, you can see “CPENT… No other Pen Test Course like it!”
Or scroll down to see “What Makes The Certified Penetration Testing Professional (CPENT) Unique?”
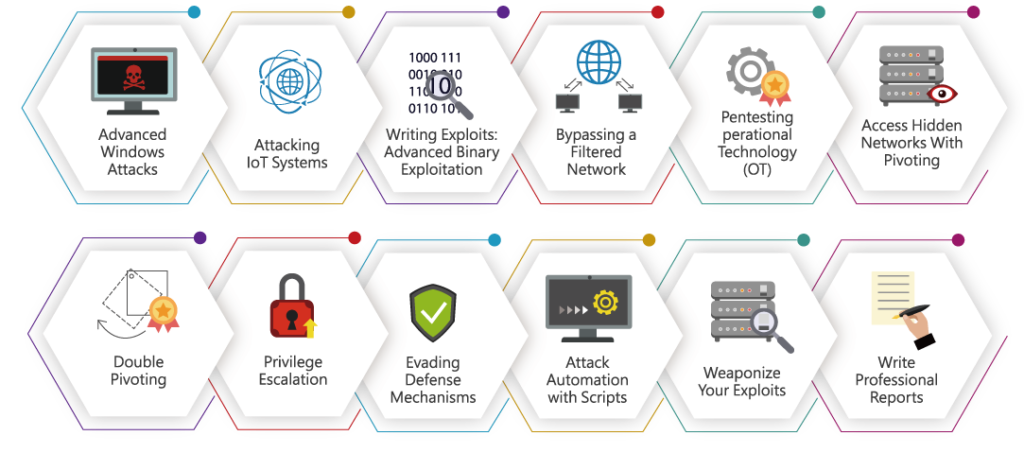
This section lists 12 items, which are essentially the exam topics. The knowledge and skills required to pass the exam are all encompassed in these 12 items. After taking the exam and reviewing these 12 items, I can confirm that the exam scope does not go beyond these topics. It is essential to master each of these items, although the difficulty level or technical requirements vary among different topics.
Exam Structure
However, the actual exam does not divide the topics into 12 sections (nor could it be divided that way). Instead, the exam is divided into five major areas: Active Directory, Binary/IOT, CTF, OT, Pivoting, and Double Pivoting. These five areas cover the aforementioned 12 topics. It is worth noting that these are five areas, not five machines or five network segments.
If you are a regular player of Hack the Box (HTB), you might be accustomed to targeting a single machine for penetration testing, gaining the highest privileges. However, in CPENT, you need to change your mindset a bit. CPENT provides you with an internal network environment with many networks and machines. You must perform host discovery on your own, and your goal is not to take down all the machines and gain root/administrator privileges. Whether you need to compromise a machine or just gather information depends on the task (some machines might not be hackable at all).
Preparation Tips
The scores for the five areas are evenly distributed. Since a score of 70% is enough to pass CPENT, even if you are not good at one area or completely give up on it, you still have a chance to pass CPENT. However, it is recommended not to give up any area. I believe the difficulty of the exam questions in each area is not very challenging, and learning more is always beneficial.
Additionally, this article focuses more on the CPENT course content and exam experience, rather than sharing the technical skills and knowledge required. For example, what tools to prepare, which syntax and techniques to be familiar with. The main reason is that if you want to take CPENT, I currently recommend enrolling in the course offered by 恆逸. The skills and knowledge required for the exam are all taught in the class. If you choose to register for the exam directly through EC-Council without taking the course (which should be possible), I think it would be challenging to pass without attending the class or having guidance; the course content is very rich.
CPENT Course
Overview
Let’s talk about the course content. I attended the CPENT course offered by 恆逸, taught by Vincent Tang Ren-Wei. The course covers penetration testing introduction, internal and external penetration processes, methodologies, and technical implementations, including AD attack methods, IoT analysis, binary analysis and buffer overflow exploitation, OT packet analysis, and web attacks, which are essentially the exam scope. If you want to map it to the chapters, it’s 01, 05, 06, 10, 11, 13, 14, and Appendix 1 (AD) in the above image. This was my second time attending Vincent’s class, and I found his teaching style very engaging and memorable, albeit occasionally a bit excitable, which aids in retention XD.

Hands-On Learning Approach
Since the exam is a practical hands-on test, many parts of the class involve the instructor teaching and demonstrating first, then allowing everyone to practice. Because the exam is hands-on, the course covers more technical “details” that would likely be overlooked if the exam were just a written multiple-choice format, such as debugging dependencies when using tools, different methods and characteristics of network pivoting, and practical implementations of Windows AD golden and silver ticket attacks.
Network Scanning Techniques
One classic and important section discussed was the details of Host Discovery and Port Scan, primarily using the well-known tool Nmap. In Network Penetration Testing, I believe understanding and being familiar with Nmap and its scanning principles is crucial. Often, after an Nmap scan, you will have an idea of which penetration methods can be tried. It’s not that Nmap is irreplaceable, but it’s so useful and powerful that there’s no reason not to learn or use it. My emphasis on Nmap stems from my own experiences.
Have you ever encountered a situation where Nmap performs host discovery, and even though the host is live, you can’t find it? Or a machine shows all 1-65535 ports open, but there are no actual services? Or scanning 1-65535 ports results in over a thousand ports being open, with different random ports each time? Or it takes over eight hours to scan the default 1000 ports in an internal network? Unfortunately, these are all issues I’ve encountered. If you don’t understand the principles of Host Discovery and Port Scan and don’t know how to debug, it’s challenging to proceed to the next step of finding and exploiting vulnerabilities.
Buffer Overflow and Binary Exploitation
Most of the course content should not be too difficult to learn with basic network, Linux skills, and cybersecurity knowledge. Moreover, in-person classes allow you to ask questions directly. The time required for preparation from finishing the course to taking the exam varies from person to person. The most challenging part of the course, in my opinion, is the Binary Exploitation section (partly because I’m not very familiar with it).
My understanding of Buffer Overflow is from preparing for the OSCP,Hands-On Learning Approach watching recommended BOF tutorials online, and practicing BOF exercises on the TryHackMe (THM) platform. This preparation covers the basic process and principles. Both OSCP and CPENT have BOF questions. I think CPENT’s BOF questions are slightly more advanced than OSCP’s. However, the two approaches are somewhat different. For those proficient in BOF, the difference between the two might not be significant. For someone like me, who prepared for the certification and is not very familiar, switching between the two can be challenging. I was confident with the OSCP BOF preparation, having successfully solved 10 THM challenges. However, transitioning from Immunity Debugger to GDB took some mental adjustment. Moving from writing shellcode to ESP to learning ROP was a bit confusing but interesting. Overall, the concepts in the BOF section are more challenging than the practical exam.
Preparation and Study Materials
The official CPENT materials include a thick book, electronic materials, online iLab, and Practice Range. The iLab has been around since ECSA, but I didn’t use it for ECSA, so I can’t compare. The iLab environment is entirely online, with both attacking machines and target environments hosted online. It offers a rich content, though with some peculiarities. Completing the iLab doesn’t guarantee passing CPENT; some chapters are similar or related to the exam, while others have low relevance. Preparing based on the instructor’s teachings is more practical. Some iLab tools are slightly outdated, and some content seems unnecessarily complicated. However, the iLab provides an excellent environment for extensive practice and testing. The classroom exercises are also conducted in the iLab.
The Practice Range simulates the exam environment. EC-Council’s view of the Practice Range is unclear, but according to the instructor, it’s for familiarizing with the exam environment before taking the test, not necessarily solving the challenges seriously. Using the Practice Range reveals many issues, such as problems with questions, answers, or machines. This is an area EC-Council needs to address and improve.
CPENT vs ECSA
CPENT is essentially a revised version of ECSA and can be considered its successor. About 70-80% of the course content remains the same between the two, with the most significant change being the shift in the exam format from multiple-choice questions to a practical, hands-on exam where you prepare your own attack machine (this is different from the CEH Practical format).
Looking at the course chapters, apart from the changes in the following four chapters, the rest of the chapter titles remain unchanged, with only minor content and slide modifications.
- The Database Penetration Testing Methodology chapter from ECSA has been removed.
CPENT has added chapters on:
- IoT Penetration Testing
- OT/SCADA Penetration Testing
- Binary Analysis and Exploitation
Although the CPENT and ECSA materials are largely similar, the change in exam format means that the course content and focus will be quite different from ECSA. Having taken the now-discontinued ECSA course, I feel fortunate because the shift to a hands-on exam means that most of the emphasis will be on the exam-relevant areas to ensure students pass the certification. This change is inevitable, as most students would prefer this mode of instruction. ECSA previously covered more practical penetration testing tips from the industry, which, although less technical, are still important. ECSA also covered a broader range of topics like social engineering, wireless, and OSINT, whereas CPENT focuses more on technical aspects, especially those related to the exam. However, both courses offer rich and solid content.
CPENT vs OSCP
Overview
The CPENT exam is quite different in nature from OSCP. The instructor often mentions this in class. However, since both are practical penetration testing certifications, comparisons are inevitable.
What does “quite different in nature” mean? It’s hard to explain, but it’s something that might seem similar to an outsider but feels different to someone in the field. For example, volleyball and beach volleyball might seem the same to a non-player, but those who play will notice the differences. Similarly, singles and doubles in tennis might seem similar, but being good at singles doesn’t guarantee success in doubles. They may seem like the same type of thing but have distinct differences that only become apparent with experience.
Reading many OSCP experience articles online, I believe that in terms of technical difficulty, OSCP is undoubtedly harder. However, in terms of preparation and passing, if you don’t take the CPENT course at Heng Yi, it might be more challenging due to the broad scope and lack of direction. Preparing for something as vast as OT can take a long time. Currently, there are only a few shared experiences online, unlike OSCP, which has many. But for those with a solid technical foundation who attend the course and practice well, passing CPENT should be fairly certain (though luck is always a factor in any exam).
Although not directly comparable, if I were to guess the difficulty level, it might be:
Self-study for CPENT > Registering for OSCP > Taking the course and exam for CPENT
Common Misconceptions
However, I want to emphasize that different certifications have varying exam styles and types, making it impossible to directly compare them or rank them. Even within the same field of penetration testing, the differences are enough that one can’t assume passing one means passing the other. The knowledge and skills required for both have significant overlap.
Misconceptions
- (X) Passing OSCP means I can definitely pass CPENT.
- (X) Passing CPENT means I can definitely pass OSCP.
Correct Perspective
- (O) Passing OSCP and the preparation process helps with CPENT, making it easier to pass next.
- (O) Passing CPENT and the preparation process helps with OSCP, making it easier to pass next.
Tools and Timing
CPENT differs from OSCP in two notable ways, which are often highlighted in their promotions and might be key points of interest for some. Firstly, CPENT allows the use of any tools, whereas OSCP restricts the use of Metasploit (only allowed once), Nessus, sqlmap, Burp Suite Professional, etc. This might be a significant concern for many. Taking this opportunity, I’d like to share my view on this matter.
When I first heard about OSCP or introduced it to others, or read discussions, everyone mentioned the restriction on Metasploit and automated scanning tools. For newcomers to the cybersecurity field, this seemed like a “strict” and “challenging” condition. But as you start learning penetration testing and gain some practical experience, you realize this restriction doesn’t have such a significant impact. Its promotional effect is much greater than the actual impact.
In my CPENT exam, I didn’t use any commercial scanning tools and only used Metasploit once (and that was out of convenience, not necessity). Most people who pass CPENT and OSCP would likely agree that even if the exam allowed Nessus, it wouldn’t be practical to use it, as it’s just a waste of time. Even when playing on HTB or THM platforms, automated scanning tools aren’t commonly used to find network or web vulnerabilities. Of course, the OSCP restriction isn’t meaningless, but it’s not as daunting as it seems.
The second difference is that CPENT allows for a choice between a single 24-hour session or two 12-hour sessions. This significantly affects the difficulty of passing the exam. The ability to split the time, regroup, and prepare during the break considerably reduces the difficulty of passing the test. For some, due to physical, family, or other reasons, taking a 24-hour exam might not be feasible, making CPENT a viable option.
CPENT Exam and Experience
I enrolled in the CPENT course in March this year. My background includes penetration testing experience, although I haven’t been exclusively doing penetration testing since the end of last year. I’ve continued working in cybersecurity, mostly in technical roles, but my penetration testing skills have inevitably become a bit rusty. To regain my touch, I subscribed to the TryHackMe (THM) platform in February to get some practice and also tackled a few Hack The Box (HTB) machines.
Once the CPENT course began, I primarily focused on practicing and reviewing the course content. The course concluded at the end of May. I also re-enrolled in the CPENT course at the end of May but only attended the Binary (BOF) part. My preparation spanned from February to April, with additional preparation in the days leading up to the exam. I took a break in May for personal reasons, so I estimate I prepared for about three months in total.
Exam Timeline
I opted for the two 12-hour sessions for the exam, which I took on June 9 and June 15. The report was submitted on June 15. During the first exam on June 9, I spent 8 hours and completed 95% of the content, leaving only the Double Pivoting question unresolved because I went down a rabbit hole with the wrong approach. Realizing this, I decided to end the exam early. On June 15, I easily resolved the remaining question, double-checked my answers and screenshots for the report, and completed the second exam in about an hour. The score is displayed immediately upon submission, and you must submit the penetration testing report within seven days of the exam. I was fortunate to score a perfect 100% on the CPENT exam and also earned the LPT Master certification.
The exam process went smoothly overall, though the designated exam time slots were only available in the afternoon, and early morning slots required sending an email to request a change, which couldn’t be done through the official system. However, my email requests were answered within a day, and communication was smooth. Another adjustment was the prohibition of using dual monitors during the exam.
Improvement
Here are a few points I believe EC-Council could improve regarding the CPENT course and exam:
- Too Much Brute Forcing: For those who regularly engage in penetration testing or work with practice machines, the number of brute force challenges is excessive. Testing for brute force on SSH, web, SMB, and RDP once each would be sufficient.
- AD Placement: Active Directory (AD) is one of the five main areas of the exam but is listed in the appendix, which is odd.
- Depth and Technical Differentiation: The inclusion of OT and IoT topics is excellent, but the depth and technical differentiation could be better. However, striking the right balance is challenging as these areas can be quite extensive.
- Privilege Escalation Variety: A bit more variation in privilege escalation would be nice. While I prefer simpler methods, having played numerous THM, HTB, and VulnHub challenges, I feel some privilege escalations are overly complex. Certifications should test penetration testing skills, not try to stump you.
Recommendation
Overall, I recommend the CPENT course and exam. Vincent’s classes are highly beneficial, providing extensive knowledge and skill-building opportunities. The practical nature of the certification exam is rare and valuable, making it worth pursuing, whether it’s CPENT, OSCP, PortSwigger’s Burp Suite certification, the Certified Red Team Professional (CRTP), or other certifications like eCPPTv2 and PNPT. Practical exams prove one’s abilities beyond theoretical knowledge. Given a Linux attack machine and a Windows vulnerable machine, being asked to exploit an RDP weak password vulnerability is one thing on a multiple-choice test, but performing it in practice involves more skills. Knowing how to brute force and connect via RDP on Linux, handling tools, and resolving dependency conflicts or special characters in passwords are all essential hands-on skills.
The practical nature of CPENT sets a basic benchmark for penetration testing capabilities. However, it doesn’t delve into highly complex techniques. Different certifications focus on various aspects, even within penetration testing. CPENT’s five-domain structure is quite balanced and distinct from other certifications.
Deciding whether to pursue certifications depends on personal goals and company requirements. Many skilled professionals might not hold any certifications. Since there are numerous certifications available and limited funds, it’s essential to choose the right one. CPENT offers a valuable entry-level assessment of penetration testing skills, and Heng Yi’s CPENT course provides practical, useful content. For those with a solid technical foundation, attending the course attentively and practicing should make passing the exam achievable. However, for experienced penetration testers or those seeking a challenge, the exam might be too straightforward.
Finally, here are my scores and certifications: CPENT & LPT Master 🙂



Thank you for taking the time to read my journey; I hope it inspires and helps you in your own path to growth.